Cybersecurity for Public Sector Fiscal Risk Use Case
Security architecture design for fiscal risk use case at Digital Agency, protecting sensitive citizen data and ensuring ENS compliance.
Category
Public Sector
Year
2024
Team size
4 people
Timeline
8 months
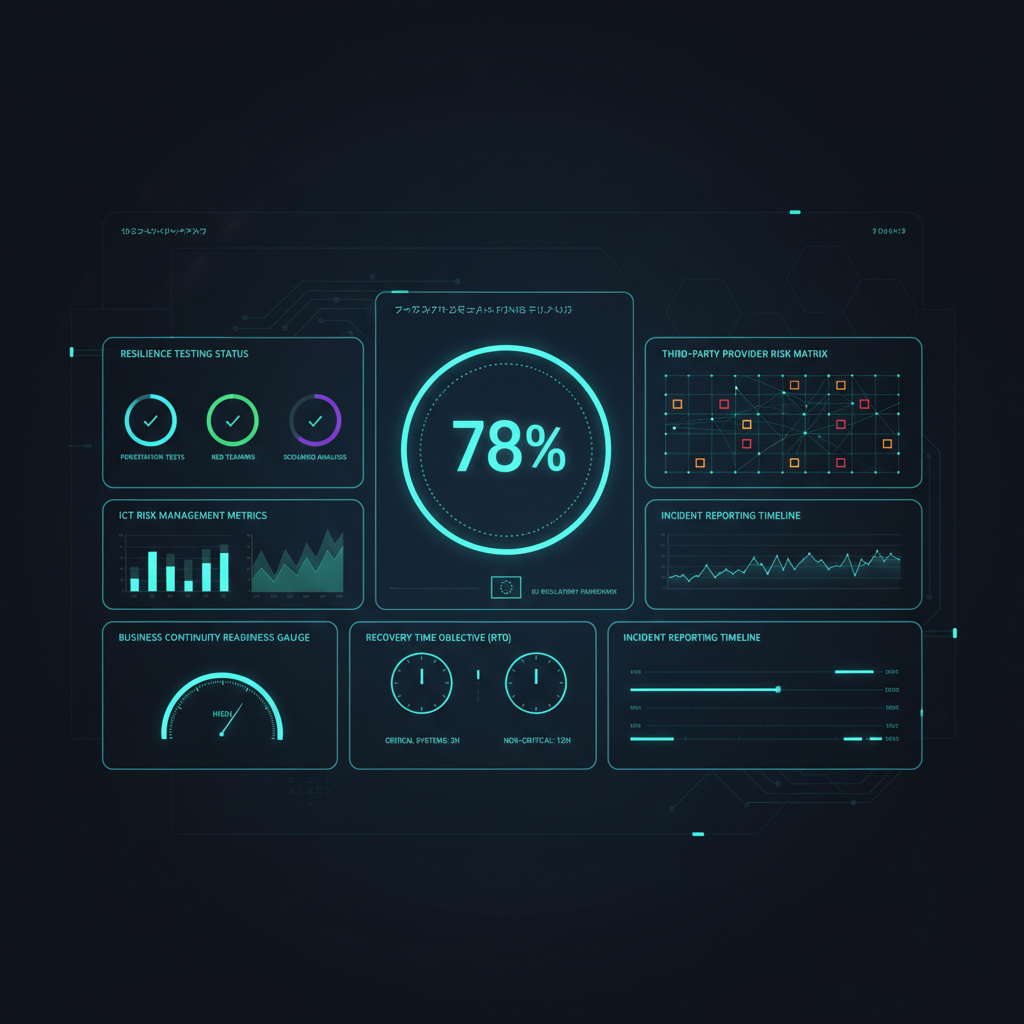
Challenge
Digitalization of the fiscal risk use case required processing sensitive tax data from millions of citizens. The system needed to comply with ENS High level, GDPR and specific fiscal regulations, while maintaining 24/7 availability and critical response times.
Solution
Defense-in-depth security architecture design specific to fiscal data, with end-to-end encryption, data segregation by sensitivity, continuous monitoring and granular access controls. Zero Trust model implementation adapted to public administration context.
Context: Public Sector Digital Transformation
The Fiscal Digitalization Challenge
The Regional Digital Agency leads public administration digital transformation. The fiscal risk use case represents one of the most sensitive projects: processing and analyzing tax data to detect risk and fraud patterns, while simultaneously protecting the privacy of millions of citizens.
Unique Security Requirements
Data to Protect:
- Tax information of 8+ million citizens
- Business and self-employed data
- Cross-references with other administrations
- Risk models (intellectual property)
Regulatory Framework:
- National Security Framework (ENS) High level
- General Data Protection Regulation (GDPR)
- Organic Law on Data Protection (LOPDGDD)
- Specific fiscal regulations
- Law 40/2015 on Public Sector Legal Regime
Security Architecture
Defense-in-Depth Model
┌─────────────────────────────────────────────────────────┐
│ Perimeter Layer │
│ WAF │ DDoS Protection │ Secure CDN │
├─────────────────────────────────────────────────────────┤
│ Network Layer │
│ Segmentation │ NSGs │ Firewall │ IDS/IPS │
├─────────────────────────────────────────────────────────┤
│ Application Layer │
│ API Gateway │ AuthN/AuthZ │ Input Validation │
├─────────────────────────────────────────────────────────┤
│ Data Layer │
│ Encryption │ Tokenization │ Masking │ DLP │
├─────────────────────────────────────────────────────────┤
│ Monitoring Layer │
│ SIEM │ Audit Logs │ Alerts │ Forensics │
└─────────────────────────────────────────────────────────┘Zero Trust for Public Administration
Applied Principles:
-
Never Trust, Always Verify
- Continuous authentication of users and services
- Context validation on every request
- No implicit access by network location
-
Least Privilege Access
- Granular roles by function
- Just-in-time access for sensitive operations
- Automated duties segregation
-
Assume Breach
- Workload microsegmentation
- Lateral movement detection
- Prepared incident response
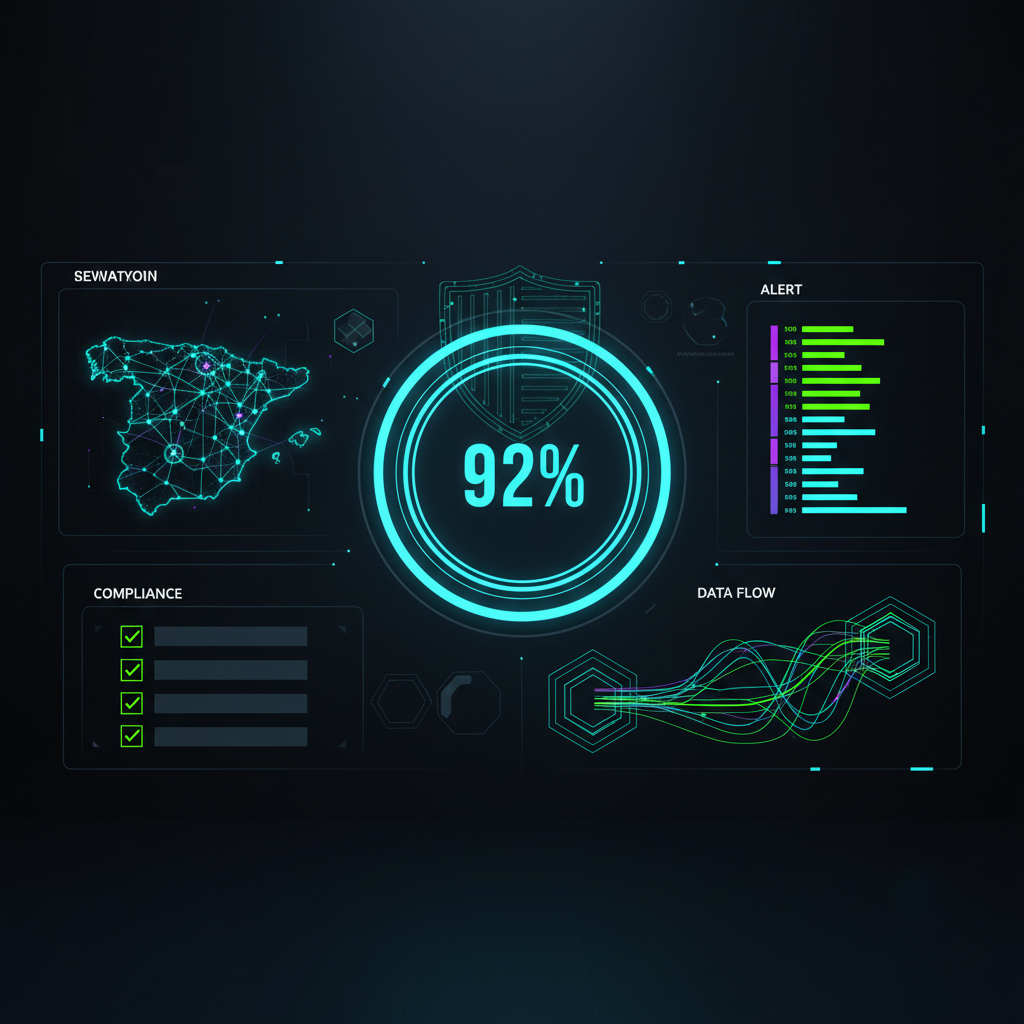
Results
Security:
- Critical vulnerabilities: 0
- Security incidents: 0 breaches
- Alert response time: < 15 min
- Monitoring coverage: 100%
Compliance:
- ENS High certification: ✓
- GDPR Compliance: Positive audit
- Audit findings: 0 critical
- Action plans: 100% closed
Operation:
- Availability: 99.97%
- Response time: < 200ms p95
- Capacity: 10M transactions/day
- Scalability: Tested at 3x load
This project demonstrated that enterprise-level security can be implemented in the public sector, protecting sensitive data of millions of citizens while enabling the digital transformation necessary for a modern and efficient administration.
Results
- ENS High level certification obtained
- GDPR compliance demonstrated in audit
- 0 data breaches since production launch
- Response time < 200ms maintained under load
- 99.97% availability in first year